Grant Thornton: Mobility – A Double Edged Sword?
 It would be hard to imagine a chef working without a culinary knife. Different kinds of knives serve different purposes. If used appropriately, these knives can do wonders for their users. However, if used carelessly or even abused, they can hurt users or in some extreme cases may be turned into weapons to hurt others.
It would be hard to imagine a chef working without a culinary knife. Different kinds of knives serve different purposes. If used appropriately, these knives can do wonders for their users. However, if used carelessly or even abused, they can hurt users or in some extreme cases may be turned into weapons to hurt others.
To a certain extent, the same can be said about the use of today’s increasingly sophisticated technology. There is no doubt that today’s technology has advanced and evolved to a point where it has become an essential ingredient of success to most businesses. It has enabled businesses to effectively reach more and more targeted customers around the world while improving efficiency of internal operations and automating interactions with their business partners both upstream and downstream.
“If left unmanaged, technology may subject companies large and small to all kinds of risks and malicious cyber-attacks, hence becoming a liability rather than an asset.”
However, if left unmanaged, technology may subject companies large and small to all kinds of risks and malicious cyber-attacks, hence becoming a liability rather than an asset. In this article, we will be focusing on one specific technology and that is enterprise mobility or simply mobility which has drawn an ample amount of attention in today’s technology driven business environment.
Definition of Mobility
When we talk about mobility in this article, we are referring to the trend towards a change in work habits, with more and more employees working remotely from the office enabled by the use of mobile devices to perform business tasks. Such devices include smart phones, tablets, and any other hand-held devices that employees carry around with them while not being in the office. These devices are usually configured to connect to the company’s internal networks thus enabling their owners or users to access computing resources of the company including critical ERP systems while on the go.
Upsides of Mobility
Since it can certainly help improve productivity and responsiveness to customer demands, organisations have come up with various ways to take advantage of mobility. For example, a deliverer that is not tech savvy can easily use his or her smart phone, either personally owned or company provided, to access the logistic module of the company’s ERP system from outside of the office to simply enter the date and time of a delivery right after the delivery to automatically trigger revenue recognition for the goods delivered.
Another use of such technology enables sales management to approve sales orders outside of the office as these workers are always out of the office in pursuit of new business opportunities with prospective customers. In addition, lower level sales personnel especially appreciate mobility as it can enable them to access their company’s warehouse or inventory management system to see if there are enough goods available in stock to meet the sales demands of their customers while also being able to check the most updated price book at real time.
Furthermore, it can also enable them to answer various inquiries from potential customers right on the spot based on information instantly accessible to them via mobility and therefore enhance the chance of obtaining new business.
Potential Pitfalls of Mobility
Now that some upsides of mobility have been discussed, let’s take a look at some of the potential pitfalls that companies need to be aware of with mobility. Physical security of these mobile devices is a legitimate concern. Mobility has enabled the expansion of the working environment outside of the traditional physical office making it possible for employees to work almost anywhere at any given time.
Physical control over computing equipment such as servers or laptops can easily be implemented in a traditional office environment. However, it would be hard for companies to safeguard these mobile devices while they are in the hands of employees being outside of the office constantly on the go.
If lost, devices may end up in the hands of individuals with malicious intents and the consequences can be disastrous as these devices may have important, sensitive, and confidential information stored on them. Worse yet, cybercriminals can gain unauthorised and sometimes privileged access through these lost devices to critical systems residing inside the company’s network potentially leading to data loss or leakage for the company.
Once inside the company’s network, these criminals will be like kids in a candy shop being able to get their hands on all the information and systems available within the network and pull off different malicious acts at their will to put the company in trouble.
Secondly, employees with hand-held mobile devices used 100% or partially for business purposes can easily fall into the trap of unintentionally installing malicious applications onto their devices potentially turning these devices into tools used by cybercriminals to gain access to the company’s internal IT environment for exploitation purposes. Uncontrolled action of such kind can put companies at great cyber security risk.
Lastly, another way employees using these mobile devices can unintentionally put their companies at risk is by connecting these devices to the Internet or even to their companies’ internal networks by using Wi-Fi provided by most coffee shops or restaurants as a complimentary service these days. As most of us are aware, Wi-Fi services at these locations are not designed to provide the most secure channels of communication. Rather, they are simply provided for the convenience of the shops’ customers for their personal casual use instead of business. Therefore, using Wi-Fi at those locations for work purposes without any secure measures in place can potentially open the door for attacks on the company’s networks.
Safeguards against Associated Risks
Now that we have considered some of the downsides of mobility, are we suggesting that mobility not be implemented at all? Absolutely not. Just as we do not stop using knives altogether simply because they can be misused, we are not suggesting that mobility be avoided at all. As a matter of fact, what we need to do is recognise the risks associated with mobility and put in place safeguards or measures to manage those risks. That way, we can reap and enjoy the benefits of mobility while minimising the associated risks.
Without getting too technical, there are indeed some safeguards that companies can implement against risks associated with mobility. We will be briefly mentioning two kinds of controls. They are administrative controls and technical controls.
Companies can mandate that the same IT security policies applicable to regular computing resources within the office be extended to cover mobile devices used by employees for business purposes. For example, companies may require employees to apply the same password policy to their mobile devices as they would their on-premise machines which may include requirements related to minimum password length, password complexity, and frequency of change.
Also, companies may require employees to refrain from installing certain applications or getting on certain websites. If necessary, companies may also make it a policy that any company-owned mobile devices assigned to employees and used for business purposes are subject to regular inspection by the IT department in order to make sure that the devices are well protected. Lastly, any requests to access company’s networks from any mobile devices need to be appropriately approved by all related parties.
Companies can implement an enterprise wide mobile device management system (MDM). In light of the increasing usage of mobile devices for work purposes, quite a few MDMs have come into existence. They can help companies manage mobile devices and provide centralised security to those devices. For smaller companies that cannot afford a MDM, there are still technical measures that can be used to help prevent data leakage from these devices. One such measure is called remote wipe. What it does is enable the device owner to remotely wipe out all the data stored on the lost device, return the device to original factory settings, or remove all programming on the device, hence rendering the device totally useless to anyone with possession of the lost device.
Assessing Pros and Cons before Implementation
Mobility is a technology that is here to stay. If implemented appropriately, it can definitely help companies become more productive, efficient, agile, and competitive. However, just as any other new technology, it does come with risks that need to be managed. One major risk has to do with data loss either due to theft or a lack of security measures applied. As such, companies need to put in place both administrative and technical measures to safeguard them against any risks associated with mobility. Lastly and most importantly, companies do well to assess the pros and cons mobility before implementation and based on that assessment, determine whether or not they are ready to embrace and adopt mobility.
By Eugene Ha and Chris Lou

Author: Eugene Ha

Author: Chris Lou
You may have an interest in also reading…
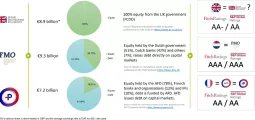
Peter Macnee: IFC Helps Virgin Mobile Find Untapped Demographic
For Mobile Virtual Network Operators (MVNO) Latin America is virgin territory. Barely 0.5% of installed network capacity is currently leased
Connecting a Country: Iraq Gears Up for a Telecoms Leap
In Iraq the budding telecom sector is to spearhead the country’s drive to full economic recovery. The Baghdad government has
WB, Vietnam Sign US$ 500 Million Loan to Improve Energy Efficiency
Hanoi, November, 2014 – The State Bank of Vietnam and the World Bank today signed a US$ 500 million loan